IPv6
| Internet protocol suite |
|---|
Application layer |
|
Transport layer |
|
Internet layer |
|
Link layer |
|
Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion. IPv6 is intended to replace IPv4.[1] IPv6 became a Draft Standard in December 1998, and became an Internet Standard on 14 July 2017.[2]
Devices on the Internet are assigned a unique IP address for identification and location definition. With the rapid growth of the Internet after commercialization in the 1990s, it became evident that far more addresses would be needed to connect devices than the IPv4 address space had available. By 1998, the Internet Engineering Task Force (IETF) had formalized the successor protocol. IPv6 uses a 128-bit address, theoretically allowing 2128, or approximately 7038340000000000000♠3.4×1038 addresses. The actual number is slightly smaller, as multiple ranges are reserved for special use or completely excluded from use. The total number of possible IPv6 addresses is more than 7028790000000000000♠7.9×1028 times as many as IPv4, which uses 32-bit addresses and provides approximately 4.3 billion addresses. The two protocols are not designed to be interoperable, complicating the transition to IPv6. However, several IPv6 transition mechanisms have been devised to permit communication between IPv4 and IPv6 hosts.
IPv6 provides other technical benefits in addition to a larger addressing space. In particular, it permits hierarchical address allocation methods that facilitate route aggregation across the Internet, and thus limit the expansion of routing tables. The use of multicast addressing is expanded and simplified, and provides additional optimization for the delivery of services. Device mobility, security, and configuration aspects have been considered in the design of the protocol.
IPv6 addresses are represented as eight groups of four hexadecimal digits with the groups being separated by colons, for example 2001:0db8:0000:0042:0000:8a2e:0370:7334, but methods to abbreviate this full notation exist.
.mw-parser-output .toclimit-2 .toclevel-1 ul,.mw-parser-output .toclimit-3 .toclevel-2 ul,.mw-parser-output .toclimit-4 .toclevel-3 ul,.mw-parser-output .toclimit-5 .toclevel-4 ul,.mw-parser-output .toclimit-6 .toclevel-5 ul,.mw-parser-output .toclimit-7 .toclevel-6 ul{display:none}
Contents
1 Main features
2 Motivation and origin
2.1 IPv4
2.2 Working-group proposals
3 Comparison with IPv4
3.1 Larger address space
3.2 Multicasting
3.3 Stateless address autoconfiguration (SLAAC)
3.4 SLAAC privacy extensions
3.5 IPsec
3.6 Simplified processing by routers
3.7 Mobility
3.8 Extension headers
3.8.1 Jumbograms
4 IPv6 packets
5 Addressing
5.1 Address representation
5.2 Address uniqueness
5.3 Link-local address
5.4 Global addressing
6 IPv6 in the Domain Name System
7 Transition mechanisms
7.1 Dual-stack IP implementation
7.2 ISP customers with public facing IPv6
7.3 Tunneling
7.3.1 IPv4-mapped IPv6 addresses
8 IPv6 readiness
8.1 Application software
8.2 Hardware and embedded systems
8.3 Shadow networks
9 Security
10 Deployment
11 See also
12 References
13 External links
Main features

Decomposition of the IPv6 address representation into its binary form
IPv6 is an Internet Layer protocol for packet-switched internetworking and provides end-to-end datagram transmission across multiple IP networks, closely adhering to the design principles developed in the previous version of the protocol, Internet Protocol Version 4 (IPv4). IPv6 was first formally described in Internet standard document .mw-parser-output cite.citation{font-style:inherit}.mw-parser-output q{quotes:"""""""'""'"}.mw-parser-output code.cs1-code{color:inherit;background:inherit;border:inherit;padding:inherit}.mw-parser-output .cs1-lock-free a{background:url("//upload.wikimedia.org/wikipedia/commons/thumb/6/65/Lock-green.svg/9px-Lock-green.svg.png")no-repeat;background-position:right .1em center}.mw-parser-output .cs1-lock-limited a,.mw-parser-output .cs1-lock-registration a{background:url("//upload.wikimedia.org/wikipedia/commons/thumb/d/d6/Lock-gray-alt-2.svg/9px-Lock-gray-alt-2.svg.png")no-repeat;background-position:right .1em center}.mw-parser-output .cs1-lock-subscription a{background:url("//upload.wikimedia.org/wikipedia/commons/thumb/a/aa/Lock-red-alt-2.svg/9px-Lock-red-alt-2.svg.png")no-repeat;background-position:right .1em center}.mw-parser-output .cs1-subscription,.mw-parser-output .cs1-registration{color:#555}.mw-parser-output .cs1-subscription span,.mw-parser-output .cs1-registration span{border-bottom:1px dotted;cursor:help}.mw-parser-output .cs1-hidden-error{display:none;font-size:100%}.mw-parser-output .cs1-visible-error{font-size:100%}.mw-parser-output .cs1-subscription,.mw-parser-output .cs1-registration,.mw-parser-output .cs1-format{font-size:95%}.mw-parser-output .cs1-kern-left,.mw-parser-output .cs1-kern-wl-left{padding-left:0.2em}.mw-parser-output .cs1-kern-right,.mw-parser-output .cs1-kern-wl-right{padding-right:0.2em}RFC 1883, published in December 1995.[3]
That RFC was obsoleted and replaced by RFC 2460, published in December 1998.[4]
In July 2017 this specification was obsoleted and replaced by RFC 8200.[5]
In addition to offering more addresses, IPv6 also implements features not present in IPv4. It simplifies aspects of address assignment (stateless address autoconfiguration), network renumbering, and router announcements when changing network connectivity providers. It simplifies processing of packets in routers by placing the responsibility for packet fragmentation into the end points. The IPv6 subnet size is standardized by fixing the size of the host identifier portion of an address to 64 bits to facilitate an automatic mechanism for forming the host identifier from link layer addressing information (MAC address). Network security was a design requirement of the IPv6 architecture, and included the original specification of IPsec.
IPv6 does not specify interoperability features with IPv4, but essentially creates a parallel, independent network. Exchanging traffic between the two networks requires translator gateways employing one of several transition mechanisms, such as NAT64, or a tunneling protocol like 6to4, 6in4, or Teredo.
Motivation and origin
IPv4
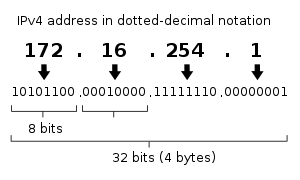
Decomposition of the quad-dotted IPv4 address representation to its binary value
Internet Protocol Version 4 (IPv4) was the first publicly used version of the Internet Protocol. IPv4 was developed as a research project by the Defense Advanced Research Projects Agency (DARPA), a United States Department of Defense agency, before becoming the foundation for the Internet and the World Wide Web. It is currently described by IETF publication RFC 791 (September 1981), which replaced an earlier definition (RFC 760, January 1980). IPv4 includes an addressing system that uses numerical identifiers consisting of 32 bits. These addresses are typically displayed in quad-dotted notation as decimal values of four octets, each in the range 0 to 255, or 8 bits per number. Thus, IPv4 provides an addressing capability of 232 or approximately 4.3 billion addresses. Address exhaustion was not initially a concern in IPv4 as this version was originally presumed to be a test of DARPA's networking concepts.[6] During the first decade of operation of the Internet, it became apparent that methods had to be developed to conserve address space. In the early 1990s, even after the redesign of the addressing system using a classless network model, it became clear that this would not suffice to prevent IPv4 address exhaustion, and that further changes to the Internet infrastructure were needed.[7]
The last unassigned top-level address blocks of 16 million IPv4 addresses were allocated in February 2011 by the Internet Assigned Numbers Authority (IANA) to the five regional Internet registries (RIRs). However, each RIR still has available address pools and is expected to continue with standard address allocation policies until one /8 Classless Inter-Domain Routing (CIDR) block remains. After that, only blocks of 1024 addresses (/22) will be provided from the RIRs to a local Internet registry (LIR). As of September 2015, all of Asia-Pacific Network Information Centre (APNIC), the Réseaux IP Européens Network Coordination Centre (RIPE_NCC), Latin America and Caribbean Network Information Centre (LACNIC), and American Registry for Internet Numbers (ARIN) have reached this stage.[8][9][10] This leaves African Network Information Center (AFRINIC) as the sole regional internet registry that is still using the normal protocol for distributing IPv4 addresses. As of November 2018, AFRINIC's minimum allocation is /22 or 1024 IPv4 addresses. A LIR may receive additional allocation when about 80% of all the address space has been utilized. [11]
Working-group proposals
By the beginning of 1992, several proposals appeared for an expanded Internet addressing system and by the end of 1992 the IETF announced a call for white papers.[12] In September 1993, the IETF created a temporary, ad-hoc IP Next Generation (IPng) area to deal specifically with such issues. The new area was led by Allison Mankin and Scott Bradner, and had a directorate with 15 engineers from diverse backgrounds for direction-setting and preliminary document review:[7][13] The working-group members were J. Allard (Microsoft), Steve Bellovin (AT&T), Jim Bound (Digital Equipment Corporation), Ross Callon (Wellfleet), Brian Carpenter (CERN), Dave Clark (MIT), John Curran (NEARNET), Steve Deering (Xerox), Dino Farinacci (Cisco), Paul Francis (NTT), Eric Fleischmann (Boeing), Mark Knopper (Ameritech), Greg Minshall (Novell), Rob Ullmann (Lotus), and Lixia Zhang (Xerox).[14]
The Internet Engineering Task Force adopted the IPng model on 25 July 1994, with the formation of several IPng working groups.[7] By 1996, a series of RFCs was released defining Internet Protocol version 6 (IPv6), starting with RFC 1883. (Version 5 was used by the experimental Internet Stream Protocol.)
It is widely expected that the Internet will use IPv4 alongside IPv6 for the foreseeable future. Direct communication between the IPv4 and IPv6 network protocols is not possible; therefore, intermediary trans-protocol systems are needed as a communication conduit between IPv4 and IPv6 whether on a single device or among network nodes.
Comparison with IPv4
On the Internet, data is transmitted in the form of network packets. IPv6 specifies a new packet format, designed to minimize packet header processing by routers.[4][15] Because the headers of IPv4 packets and IPv6 packets are significantly different, the two protocols are not interoperable. However, in most respects, IPv6 is an extension of IPv4. Most transport and application-layer protocols need little or no change to operate over IPv6; exceptions are application protocols that embed Internet-layer addresses, such as File Transfer Protocol (FTP) and Network Time Protocol (NTP), where the new address format may cause conflicts with existing protocol syntax.
Larger address space
The main advantage of IPv6 over IPv4 is its larger address space. The length of an IPv6 address is 128 bits, compared with 32 bits in IPv4.[4] The address space therefore has 2128 or approximately 7038340000000000000♠3.4×1038 addresses (340,282,366,920,938,463,463,374,607,431,768,211,456, which is approximately 340 undecillion, or 340 billion billion billion billion, addresses).
In addition, the IPv4 address space is poorly allocated; in 2011, approximately 14% of all available addresses were utilized.[16] While these numbers are large, it was not the intent of the designers of the IPv6 address space to assure geographical saturation[clarification needed] with usable addresses. Rather, the longer addresses simplify allocation of addresses, enable efficient route aggregation, and allow implementation of special addressing features. In IPv4, complex Classless Inter-Domain Routing (CIDR) methods were developed to make the best use of the small address space. The standard size of a subnet in IPv6 is 264 addresses, the square of the size of the entire IPv4 address space. Thus, actual address space utilization rates will be small in IPv6, but network management and routing efficiency are improved by the large subnet space and hierarchical route aggregation.
Renumbering an existing network for a new connectivity provider with different routing prefixes is a major effort with IPv4.[17][18] With IPv6, however, changing the prefix announced by a few routers can in principle renumber an entire network, since the host identifiers (the least-significant 64 bits of an address) can be independently self-configured by a host.[19]
Multicasting
Multicasting, the transmission of a packet to multiple destinations in a single send operation, is part of the base specification in IPv6. In IPv4 this is an optional (although commonly) implemented feature.[20] IPv6 multicast addressing has features and protocols in common with IPv4 multicast, but also provides changes and improvements by eliminating the need for certain protocols. IPv6 does not implement traditional IP broadcast, i.e. the transmission of a packet to all hosts on the attached link using a special broadcast address, and therefore does not define broadcast addresses. In IPv6, the same result is achieved by sending a packet to the link-local all nodes multicast group at address ff02::1, which is analogous to IPv4 multicasting to address 224.0.0.1. IPv6 also provides for new multicast implementations, including embedding rendezvous point addresses in an IPv6 multicast group address, which simplifies the deployment of inter-domain solutions.[21]
In IPv4 it is very difficult for an organization to get even one globally routable multicast group assignment, and the implementation of inter-domain solutions is arcane.[22] Unicast address assignments by a local Internet registry for IPv6 have at least a 64-bit routing prefix, yielding the smallest subnet size available in IPv6 (also 64 bits). With such an assignment it is possible to embed the unicast address prefix into the IPv6 multicast address format, while still providing a 32-bit block, the least significant bits of the address, or approximately 4.2 billion multicast group identifiers. Thus each user of an IPv6 subnet automatically has available a set of globally routable source-specific multicast groups for multicast applications.[23]
Stateless address autoconfiguration (SLAAC)
IPv6 hosts can configure themselves automatically when connected to an IPv6 network using the Neighbor Discovery Protocol via Internet Control Message Protocol version 6 (ICMPv6) router discovery messages. When first connected to a network, a host sends a link-local router solicitation multicast request for its configuration parameters; routers respond to such a request with a router advertisement packet that contains Internet Layer configuration parameters.[19] Routers present a special case of requirements for address configuration, as they often are sources of autoconfiguration information, such as router and prefix advertisements. Stateless configuration of routers can be achieved with a special router renumbering protocol.[24]
If IPv6 stateless address auto-configuration is unsuitable, IPv6 just like IPv4 allows for stateful configuration with the Dynamic Host Configuration Protocol version 6 (DHCPv6) or manual static configuration of hosts.
SLAAC privacy extensions
Like IPv4, IPv6 supports globally unique IP addresses. The design of IPv6 intended to re-emphasize the end-to-end principle of network design that was originally conceived during the establishment of the early Internet. In this approach each device on the network has a unique address globally reachable directly from any other location on the Internet.
A unique IP address can potentially be used to track the network activity of a device. Moreover, when using IPv6 address auto-configuration, the Interface Identifier (MAC address) of a network card is used to make its public IPv6 interface identifier unique, exposing the type of hardware used and providing a unique handle for a user's online activity.[citation needed] Autoconfiguration on the basis of the network card MAC address is therefore a particular privacy concern for mobile devices, such as laptops, because when they access the Internet from different local area networks, their MAC based interface identifier would always stay the same. Thus the MAC address based interface identifier can be used to track the movement and usage of a particular mobile device.[25]
When IPv6 was developed in the mid-90s, the Internet was not accessed by a large number of mobile devices and privacy was not the priority it has become today. To address these privacy concerns, the SLAAC protocol was updated with mechanisms that were termed “Privacy Extensions for Stateless Address Autoconfiguration in IPv6”, codified in RFC 4941. This allows for the IPv6 address interface identifier to be generated randomly. If the same interface identifier is generated for two devices in the same local area network, the Duplicate Address Detection (DAD) function of the IPv6 Neighbor Discovery Protocol (NDP) will resolve the situation. The SLAAC privacy extension also implements a time out, which is configurable, so that the IPv6 interface addresses will be discarded and a new interface identifier is generated. Typically the time out is configured to 24 hours. So IPv6 autoconfiguration will generate and set a new IPv6 host address every day. As of late 2014 the SLAAC privacy extensions functionality was implemented by the following operating systems: all Microsoft Windows after Windows XP, all versions of Mac OS X from 10.7 onward, all versions of iOS since 4.3, all versions of Android since 4.0 (Ice Cream Sandwich).[26] The privacy extension is now enabled by default in Windows (since XP SP1), OS X (since 10.7), and iOS (since version 4.3).[27][28] Some Linux distributions have enabled privacy extensions as well.[29]
IPsec
Internet Protocol Security (IPsec) was originally developed for IPv6, but found widespread deployment first in IPv4, for which it was re-engineered. IPsec was a mandatory part of all IPv6 protocol implementations,[4] and Internet Key Exchange (IKE) was recommended, but with RFC 6434 the inclusion of IPsec in IPv6 implementations was downgraded to a recommendation because it was considered impractical to require full IPsec implementation for all types of devices that may use IPv6. However, as of RFC 4301 IPv6 protocol implementations that do implement IPsec need to implement IKEv2 and need to support a minimum set of cryptographic algorithms. This requirement will help to make IPsec implementations more interoperable between devices from different vendors. The IPsec Authentication Header (AH) and the Encapsulating Security Payload header (ESP) are implemented as IPv6 extension headers.[30]
Simplified processing by routers
The packet header in IPv6 is simpler than the IPv4 header. Many rarely used fields have been moved to optional header extensions.[31] With the simplified IPv6 packet header the process of packet forwarding by routers has been simplified. Although IPv6 packet headers are at least twice the size of IPv4 packet headers, packet processing by routers is generally more efficient, because less processing is required in routers due to the headers being aligned to match common word sizes.[4][15]
Moreover, an IPv6 header does not include a checksum. The IPv4 header checksum is calculated for the IPv4 header, and has to be recalculated by routers every time the time to live (called hop limit in the IPv6 protocol) is reduced by one. The absence of a checksum in the IPv6 header furthers the end-to-end principle of Internet design, which envisioned that most processing in the network occurs in the leaf nodes. Integrity protection for the data that is encapsulated in the IPv6 packet is assumed to be assured by both the link layer or error detection in higher-layer protocols, namely the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) on the transport layer. Thus, while IPv4 allowed UDP datagram headers to have no checksum (indicated by 0 in the header field), IPv6 requires a checksum in UDP headers.
IPv6 routers do not perform IP fragmentation. IPv6 hosts are required to either perform path MTU discovery, perform end-to-end fragmentation, or to send packets no larger than the default Maximum transmission unit (MTU), which is 1280 octets.
Mobility
Unlike mobile IPv4, mobile IPv6 avoids triangular routing and is therefore as efficient as native IPv6. IPv6 routers may also allow entire subnets to move to a new router connection point without renumbering.[32]
Extension headers
The IPv6 packet header has a minimum size of 40 octets (320 bits). Options are implemented as extensions. This provides the opportunity to extend the protocol in the future without affecting the core packet structure.[4] However, a study in 2015 indicated that some network operators dropped IPv6 packets with extension headers when they traversed transit autonomous systems.[33]
Jumbograms
IPv4 limits packets to 65,535 (216−1) octets of payload. An IPv6 node can optionally handle packets over this limit, referred to as jumbograms, which can be as large as 4,294,967,295 (232−1) octets. The use of jumbograms may improve performance over high-MTU links. The use of jumbograms is indicated by the Jumbo Payload Option extension header.[34]
IPv6 packets

IPv6 packet header
An IPv6 packet has two parts: a header and payload.
The header consists of a fixed portion with minimal functionality required for all packets and may be followed by optional extensions to implement special features.
The fixed header occupies the first 40 octets (320 bits) of the IPv6 packet. It contains the source and destination addresses, traffic classification options, a hop counter, and the type of the optional extension or payload which follows the header. This Next Header field tells the receiver how to interpret the data which follows the header. If the packet contains options, this field contains the option type of the next option. The "Next Header" field of the last option, points to the upper-layer protocol that is carried in the packet's payload.
Extension headers carry options that are used for special treatment of a packet in the network, e.g., for routing, fragmentation, and for security using the IPsec framework.
Without special options, a payload must be less than 64KB. With a Jumbo Payload option (in a Hop-By-Hop Options extension header), the payload must be less than 4 GB.
Unlike with IPv4, routers never fragment a packet. Hosts are expected to use Path MTU Discovery to make their packets small enough to reach the destination without needing to be fragmented. See IPv6 packet fragmentation.
Addressing
IPv6 addresses have 128 bits. The design of the IPv6 address space implements a very different design philosophy than in IPv4, in which subnetting was used to improve the efficiency of utilization of the small address space. In IPv6, the address space is deemed large enough for the foreseeable future, and a local area subnet always uses 64 bits for the host portion of the address, designated as the interface identifier, while the most-significant 64 bits are used as the routing prefix.[35]
The identifier is only unique within the subnet to which a host is connected. IPv6 has a mechanism for automatic address detection,[36] so that address autoconfiguration always produces unique assignments.
Address representation
The 128 bits of an IPv6 address are represented in 8 groups of 16 bits each. Each group is written as four hexadecimal digits (sometimes called hextets[37][38] or more formally a hexadectets[39] and informally a quibble or quad-nibble [39]) and the groups are separated by colons (:). An example of this representation is 2001:0db8:0000:0000:0000:ff00:0042:8329.
For convenience, an IPv6 address may be abbreviated to shorter notations by application of the following rules.
- One or more leading zeroes from any groups of hexadecimal digits are removed; this is usually done to either all or none of the leading zeroes. For example, the group 0042 is converted to 42.
- Consecutive sections of zeroes are replaced with a double colon (::). The double colon may only be used once in an address, as multiple use would render the address indeterminate.
RFC 5952 recommends that a double colon not be used to denote an omitted single section of zeroes.[40]
An example of application of these rules:
- Initial address: 2001:0db8:0000:0000:0000:ff00:0042:8329
- After removing all leading zeroes in each group: 2001:db8:0:0:0:ff00:42:8329
- After omitting consecutive sections of zeroes: 2001:db8::ff00:42:8329
The loopback address, 0000:0000:0000:0000:0000:0000:0000:0001, may be abbreviated to ::1 by using both rules.
As an IPv6 address may have more than one representation, the IETF has issued a proposed standard for representing them in text.[41]
Address uniqueness
Hosts verify the uniqueness of addresses assigned by sending a neighbor solicitation message asking for the Link Layer address of the IP address. If any other host is using that address, it responds. However, MAC addresses are designed to be unique on each network card which minimizes chances of duplication.[42]
The host first determines if the network is connected to any routers at all, because if not, then all nodes are reachable using the link-local address that already is assigned to the host. The host will send out a Router Solicitation message to the all-routers[43][44] multicast group with its link-local address as source. If there is no answer after a predetermined number of attempts, the host concludes that no routers are connected. If it does get a response from a router, there will be network information inside that is needed to create a globally unique address. There are also two flag bits that tell the host whether it should use DHCP to get further information and addresses:
- The Manage bit, that indicates whether or not the host should use DHCP to obtain additional addresses
- The Other bit, that indicates whether or not the host should obtain other information through DHCP. The other information consists of one or more prefix information options for the subnets that the host is attached to, a lifetime for the prefix, and two flags:[42]
- On-link: If this flag is set, the host will treat all addresses on the specific subnet as being on-link, and send packets directly to them instead of sending them to a router for the duration of the given lifetime.
- Address: This is the flag that tells the host to actually create a global address.
Link-local address
All interfaces of IPv6 hosts require a link-local address. A link-local address is derived from the MAC address of the interface and the prefix fe80::/10. The process involves filling the address space with prefix bits left-justified to the most-significant bit, and filling the MAC address in EUI-64 format into the least-significant bits. If any bits remain to be filled between the two parts, those are set to zero.[36]
The uniqueness of the address on the subnet is tested with the Duplicate Address Detection (DAD) method.[45]
Global addressing
The assignment procedure for global addresses is similar to local address construction. The prefix is supplied from router advertisements on the network. Multiple prefix announcements cause multiple addresses to be configured.[42]
Stateless address autoconfiguration (SLAAC) requires a /64 address block, as defined in RFC 4291. Local Internet registries are assigned at least /32 blocks, which they divide among subordinate networks.[46] The initial recommendation stated assignment of a /48 subnet to end-consumer sites (RFC 3177). This was replaced by RFC 6177, which "recommends giving home sites significantly more than a single /64, but does not recommend that every home site be given a /48 either". /56s are specifically considered. It remains to be seen if ISPs will honor this recommendation. For example, during initial trials, Comcast customers were given a single /64 network.[47]
IPv6 addresses are classified by three types of networking methodologies: unicast addresses identify each network interface, anycast addresses identify a group of interfaces, usually at different locations of which the nearest one is automatically selected, and multicast addresses are used to deliver one packet to many interfaces. The broadcast method is not implemented in IPv6. Each IPv6 address has a scope, which specifies in which part of the network it is valid and unique. Some addresses are unique only on the local (sub-)network. Others are globally unique.
Some IPv6 addresses are reserved for special purposes, such as loopback, 6to4 tunneling, and Teredo tunneling, as outlined in RFC 5156. Also, some address ranges are considered special, such as link-local addresses for use on the local link only, Unique local addresses (ULA), as described in RFC 4193, and solicited-node multicast addresses used in the Neighbor Discovery Protocol.
IPv6 in the Domain Name System
In the Domain Name System, hostnames are mapped to IPv6 addresses by AAAA resource records, so-called quad-A records. For reverse resolution, the IETF reserved the domain ip6.arpa, where the name space is hierarchically divided by the 1-digit hexadecimal representation of nibble units (4 bits) of the IPv6 address. This scheme is defined in RFC 3596.
At the design stage of the IPv6 DNS architecture, the AAAA scheme faced a rival proposal. This alternate approach, designed to facilitate network renumbering, uses A6 records for the forward lookup and a number of other innovations such as bit-string labels and DNAME records. It is defined in RFC 2874 and its references (with further discussion of the pros and cons of both schemes in RFC 3364), but has been deprecated to experimental status (RFC 3363).
Transition mechanisms
IPv6 is not foreseen to supplant IPv4 instantaneously. Both protocols will continue to operate simultaneously for some time. Therefore, IPv6 transition mechanisms are needed to enable IPv6 hosts to reach IPv4 services and to allow isolated IPv6 hosts and networks to reach each other over IPv4 infrastructure.[48]
According to Silvia Hagen, a dual-stack implementation of the IPv4 and IPv6 on devices is the easiest way to migrate to IPv6.[49] Many other transition mechanisms use tunneling to encapsulate IPv6 traffic within IPv4 networks and vice versa. This is an imperfect solution, which reduces the maximum transmission unit (MTU) of a link and therefore complicates Path MTU Discovery, and may increase latency.[50][51]
Dual-stack IP implementation
Dual-stack IP implementations provide complete IPv4 and IPv6 protocol stacks in the same network node on top of the common physical layer implementation, such as Ethernet. This permits dual-stack hosts to participate in IPv6 and IPv4 networks simultaneously. The method is defined in RFC 4213.[52]
A device with dual-stack implementation has an IPv4 and IPv6 address, and can communicate with other nodes in the LAN or the Internet using either IPv4 or IPv6. The Domain Name System (DNS) protocol is used by both IP implementations to resolve fully qualified domain names (FQDN) and IP addresses, but dual stack requires that the resolving DNS server can resolve both types of addresses. Such a dual stack DNS server would hold IPv4 addresses in the A records, and IPv6 addresses in the AAAA records. Depending on the destination that is to be resolved, a DNS name server may return an IPv4 or IPv6 IP address, or both. A default address selection mechanism, or preferred protocol, needs to be configured either on hosts or the DNS server. The IETF has published Happy Eyeballs to assist dual stack applications, so that they can connect using both IPv4 and IPv6, but prefer an IPv6 connection if it is available. Dual-stack also needs to be implemented on routers, so that they can forward IPv6 packets using the IPv6 versions of routing protocols. When dual stack networks protocols are in place the application layer can be migrated to IPv6.[53]
However, outdated DNS server implementations don’t support IPv6. While dual-stack is supported by major operating system and network device vendors, legacy networking hardware and servers don't support IPv6.
ISP customers with public facing IPv6

IPv6 Prefix Assignment mechanism with IANA, RIRs, and ISPs.
Internet service providers (ISPs) are increasingly providing their business and private customers with public facing IPv6 global unicast addresses. However, if in the local area network (LAN) IPv4 is still used, and the ISP can only provide a public facing IPv6, the IPv4 LAN addresses are translated into the public facing IPv6 address using NAT64, a network address translation (NAT) mechanism. Some ISPs cannot provide their customers with a public facing IPv4 and IPv6, thus supporting dual stack, because some ISPs have run out of IPv4 addresses that are globally routable. Meanwhile, ISP customers are still trying to reach web servers and other destinations that have an IPv4 address.[54]
IPv6 addresses are in the process of being allocated all over the world. A significant percentage of ISPs in all Regional Internet Registry (RIR) zones have already obtained IPv6 address space. This includes many of the world’s major ISPs and mobile network operators, such as Verizon Wireless, StarHub Cable, Chubu Telecommunications, Kabel Deutschland, Swisscom, T-Mobile, Internode and Telefonica.[55]
While there are still some ISPs that only allocate their DSL customers an IPv4, many ISPs allocate their customers only an IPv6 or dual stack IPv4 and IPv6. ISPs report the share of IPv6 traffic from customers over their network to be anything between 20% and 40%, but by mid-2017 IPv6 traffic still only accounted for a fraction of total traffic at several large Internet exchange points (IXPs). AMS-IX reported it to be 2% and SeattleIX reported 7%. A 2017 survey found that many DSL customers that were served by a dual stack ISP did not request DNS servers to resolve fully qualified domain names into IPv6 addresses. The survey also found that the majority of traffic from IPv6-ready webserver resources were still requested and served over IPv4, mostly due to ISP customers that did not use the dual stack facility provided by their ISP and to a lesser extent due to customers of IPv4-only ISPs.[56]
Tunneling
The technical basis for tunneling, or encapsulating IPv6 packets in IPv4 packets, is outlined in RFC 4213. When the Internet backbone was IPv4 only one of the frequently used tunneling protocols was 6to4.[57]Teredo tunneling was also frequently used for integrating IPv6 LANs with the IPv4 Internet backbone. Teredo is outlined in RFC 4380 and allows IPv6 local area networks to tunnel over IPv4 networks, by encapsulating IPv6 packets within UDP. The Teredo relay is an IPv6 router that mediates between a Teredo server and the native IPv6 network. It was expected that 6to4 and Teredo would be widely deployed until ISP networks would switch to native IPv6, but by 2014 Google Statistics showed that the use of both mechanisms had dropped to almost 0.[58]
IPv4-mapped IPv6 addresses
Hybrid dual-stack IPv6/IPv4 implementations recognize a special class of addresses, the IPv4-mapped IPv6 addresses. These addresses consist of an 80-bit prefix of zeros, the next 16 bits are ones, and the remaining, least-significant 32 bits contain the IPv4 address. These addresses are typically written with a 96-bit prefix in the standard IPv6 format, and the remaining 32 bits written in the customary dot-decimal notation of IPv4. For example, ::ffff:192.0.2.128 represents the IPv4 address 192.0.2.128. A deprecated format for IPv4-compatible IPv6 addresses is ::192.0.2.128.[59]
Because of the significant internal differences between IPv4 and IPv6, some of the lower-level functionality available to programmers in the IPv6 stack does not work the same when used with IPv4-mapped addresses. Some common IPv6 stacks do not implement the IPv4-mapped address feature, either because the IPv6 and IPv4 stacks are separate implementations (e.g., Microsoft Windows 2000, XP, and Server 2003), or because of security concerns (OpenBSD).[60] On these operating systems, a program must open a separate socket for each IP protocol it uses. On some systems, e.g., the Linux kernel, NetBSD, and FreeBSD, this feature is controlled by the socket option IPV6_V6ONLY, as specified in RFC 3493.[61]
IPv6 readiness
Compatibility with IPv6 networking is mainly a software or firmware issue. However, much of the older hardware that could in principle be upgraded is likely to be replaced instead. In 2010, the American Registry for Internet Numbers (ARIN) suggested that all Internet servers be prepared to serve IPv6-only clients by January 2012.[62]
Application software
Host software may have only IPv4 or only IPv6 networking software, or it may support dual-stack, or hybrid dual-stack operation. All personal computers and smartphones running recent major operating system versions support IPv6. Many popular applications with networking capabilities are compliant. Some software transitioning mechanisms are outlined in RFC 4038, RFC 3493, and RFC 3542.
Hardware and embedded systems
The CableLabs consortium published the 160 Mbit/s DOCSIS 3.0 IPv6-ready specification for cable modems in August 2006. DOCSIS 2.0 was updated as DOCSIS 2.0 + IPv6 to provide IPv6 support, which may be available with a firmware upgrade.[63][64]
Shadow networks
The addition of nodes having IPv6 enabled by default by the software manufacturer, may result in the inadvertent creation of shadow networks, causing IPv6 traffic flowing into networks having only IPv4 security management in place. This may also occur with operating system upgrades, when the newer operating system enables IPv6 by default, while the older one did not. Failing to update the security infrastructure to accommodate IPv6 can lead to IPv6 traffic bypassing it.[65] Shadow networks have occurred on business networks in which enterprises are replacing Windows XP systems that do not have an IPv6 stack enabled by default, with Windows 7 systems, that do.[66] Some IPv6 stack implementors have therefore recommended disabling IPv4 mapped addresses and instead using a dual-stack network where supporting both IPv4 and IPv6 is necessary.[67]
Security
Research has shown that the use of fragmentation can be leveraged to evade network security controls, similar to IPv4. As a result, RFC 7112 requires that the first fragment of an IPv6 packet contains the entire IPv6 header chain, such that some very pathological fragmentation cases are forbidden. Additionally, as a result of research on the evasion of RA-Guard in RFC 7113, RFC 6980 has deprecated the use of fragmentation with Neighbor Discovery, and discouraged the use of fragmentation with Secure Neighbor Discovery (SEND).
Deployment
The 1993 introduction of Classless Inter-Domain Routing (CIDR) in the routing and IP address allocation for the Internet, and the extensive use of network address translation (NAT), delayed IPv4 address exhaustion. The final phase of exhaustion started on 3 February 2011.[68] However, despite a decade long development and implementation history as a Standards Track protocol, general worldwide deployment of IPv6 is increasing slowly. As of September 2013[update], about 4% of domain names and 16.2% of the networks on the Internet had IPv6 protocol support.[69]
IPv6 has been implemented on all major operating systems in use in commercial, business, and home consumer environments. Since 2008, the domain name system can be used in IPv6. IPv6 was first used in a major world event during the 2008 Summer Olympic Games,[70] the largest showcase of IPv6 technology since the inception of IPv6.[71] Some governments including the Federal government of the United States and China have issued guidelines and requirements for IPv6 capability.
In 2009, Verizon mandated IPv6 operation, and reduced IPv4 to an optional capability, for LTE cellular hardware.[72] As of June 2012[update], T-Mobile USA also supports external IPv6 access.[73]
As of 2014, IPv4 still carried more than 99% of worldwide Internet traffic.[74][75] The Internet exchanges in Amsterdam and Seattle are the only large exchanges that publicly show IPv6 traffic statistics, which as of October 2018 are tracking at about 2.9% and 7.7%, growing at about 1.9% and -2.6% per year, respectively.[76][77] As of 17 November 2018[update], the percentage of users reaching Google services with IPv6 reached 26.0% for the first time, growing at about 4.7% per year. This growth is down from 7.2% per year between July 2016 and July 2017.[78] As of November 2018[update] about 26% of Alexa Top 1000 web servers support IPv6.[79]
See also
- DHCPv6
- China Next Generation Internet
- Comparison of IPv6 support in operating systems
- Comparison of IPv6 support in common applications
- DoD IPv6 product certification
- Happy Eyeballs
- List of IPv6 tunnel brokers
- University of New Hampshire InterOperability Laboratory
References
^ New Zealand IPv6 Task Force. "FAQs". Retrieved 26 October 2015.
^ Siddiqui, Aftab (17 July 2017). "RFC 8200 – IPv6 has been standardized". Internet Society. Retrieved 25 February 2018.
^ S. Deering; R. Hinden (December 1995), Internet Protocol, Version 6 (IPv6) Specification, Internet Engineering Task Force (IETF), RFC 1883
^ abcdef S. Deering; R. Hinden (December 1998), Internet Protocol, Version 6 (IPv6) Specification, Internet Engineering Task Force (IETF), RFC 2460 Obsoletes RFC 1883.
^ S. Deering; R. Hinden (July 2017), Internet Protocol, Version 6 (IPv6) Specification, Internet Engineering Task Force (IETF), ISSN 2070-1721, RFC 8200 Obsoletes RFC 2460.
^ Google IPv6 Conference 2008: What will the IPv6 Internet look like?. Event occurs at 13:35.
^ abc Bradner, S.; Mankin, A. (January 1995). The Recommendation for the IP Next Generation Protocol. IETF. doi:10.17487/RFC1752. RFC 1752. https://tools.ietf.org/html/rfc1752.
^ Rashid, Fahmida. "IPv4 Address Exhaustion Not Instant Cause for Concern with IPv6 in Wings". eWeek. Retrieved 23 June 2012.
^ Ward, Mark. "Europe hits old internet address limits". BBC. Retrieved 15 September 2012.
^ Huston, Geoff. "IPV4 Address Report".
^ "African Network Information Center : -". my.afrinic.net. Retrieved 2018-11-28.
^ Bradner, S.; Mankin, A. (December 1993). "IP: Next Generation (IPng) White Paper Solicitation". RFC 1550.
^ "History of the IPng Effort". Sun.
^ "The Recommendation for the IP Next Generation Protocol – Appendix B". RFC 1752.
^ ab Partridge, C.; Kastenholz, F. (December 1994). "Technical Criteria for Choosing IP The Next Generation (IPng)". RFC 1726.
^ "Moving to IPv6: Now for the hard part (FAQ)". Deep Tech. CNET News. Retrieved 3 February 2011.
^ Ferguson, P.; Berkowitz, H. (January 1997). "Network Renumbering Overview: Why would I want it and what is it anyway?". RFC 2071.
^ Berkowitz, H. (January 1997). "Router Renumbering Guide". RFC 2072.
^ ab Thomson, S.; Narten, T.; Jinmei, T. (September 2007). "IPv6 Stateless Address Autoconfiguration". RFC 4862.
^
RFC 1112, Host extensions for IP multicasting, S. Deering (August 1989)
^
RFC 3956, Embedding the Rendezvous Point (RP) Address in an IPv6 Multicast Address, P. Savola, B. Haberman (November 2004)
^
RFC 2908, The Internet Multicast Address Allocation Architecture, D. Thaler, M. Handley, D. Estrin (September 2000)
^
RFC 3306, Unicast-Prefix-based IPv6 Multicast Addresses, B. Haberman, D. Thaler (August 2002)
^
RFC 2894, Router Renumbering for IPv6, M. Crawford, August 2000.
^ T. Narten, R. Draves & S. Krishnan (September 2007). "Privacy Extensions for Stateless Address Autoconfiguration in IPv6". www.ietf.org. Retrieved 13 March 2017.CS1 maint: Uses authors parameter (link)
^ T. Narten, R. Draves & S. Krishnan (8 August 2014). "Privacy Extensions for IPv6 SLAAC". www.internetsociety.org. Retrieved 13 March 2017.CS1 maint: Uses authors parameter (link)
^ Overview of the Advanced Networking Pack for Windows XP, Revision: 8.14
^ IPv6: Privacy Extensions einschalten, Reiko Kaps, 13 April 2011
^ "Comment #61 : Bug #176125 : Bugs: "procps" package: Ubuntu". Bugs.launchpad.net. Retrieved 19 February 2012.
^ Silvia Hagen (2014). IPv6 Essentials: Integrating IPv6 Into Your IPv4 Network. O'Reilly Media. p. 196. ISBN 978-1-4493-3526-7.
^ "The History of Domain Names | IPv6". www.historyofdomainnames.com. Retrieved 2018-06-12.
^
RFC 3963, Network Mobility (NEMO) Basic Protocol Support, V. Devarapalli, R. Wakikawa, A. Petrescu, P. Thubert (January 2005)
^ Gont, F.; Linkova, J.; Chown, T.; Liu, S. (October 2015). "Observations on the Dropping of Packets with IPv6 Extension Headers in the Real World". draft-ietf-v6ops-ipv6-ehs-in-real-world-01.
^
RFC 2675, IPv6 Jumbograms, D. Borman, S. Deering, R. Hinden (August 1999)
^
RFC 4291, p. 9
^ ab
RFC 3315, R. Droms, J. Bound, B. Volz, T. Lemon, C. Perkins, and M. Carney, Dynamic Host Configuration Protocol for IPv6 (DHCPv6), July 2003 (Proposed Standard)
^ Graziani, Rick (2012). IPv6 Fundamentals: A Straightforward Approach to Understanding IPv6. Cisco Press. p. 55. ISBN 978-0-13-303347-2.
^ Coffeen, Tom (2014). IPv6 Address Planning: Designing an Address Plan for the Future. O'Reilly Media. p. 170. ISBN 978-1-4919-0326-1.
^ ab Horley, Edward (2013). Practical IPv6 for Windows Administrators. Apress. p. 17. ISBN 978-1-4302-6371-5.
^ S. Kawamura (August 2010). "A Recommendation for IPv6 Address Text Representation". section 4.2.2. RFC 5952.
^ S. Kawamura (August 2010). "A Recommendation for IPv6 Address Text Representation". RFC 5952. Missing or empty|url=(help)
^ abc Narten, T. (August 1999). "Neighbor discovery and stateless autoconfiguration in IPv6". IEEE Internet Computing. 3 (4): 54–62. doi:10.1109/4236.780961.
^ S. Thomson (September 2007). "IPv6 Stateless Address Autoconfiguration". section 5.5.1. RFC 4862.
^ T. Narten (September 2007). "Neighbor Discovery for IP version 6 (IPv6)". section 6.3.7. RFC 4861.
^ S. Thomson; T. Narten; T. Jinmei (September 2007). "IPv6 Stateless Address Autoconfiguration". RFC 4862.
^ "IPv6 Address Allocation and Assignment Policy". RIPE NCC. 8 February 2011. Retrieved 27 March 2011.
^ "Comcast Activates First Users With IPv6 Native Dual Stack Over DOCSIS". Comcast.com. Comcast. 31 January 2011.
^ "IPv6 Transition Mechanism / Tunneling Comparison". Sixxs.net. Retrieved 20 January 2012.
^ Silvia Hagen (2014). IPv6 Essentials: Integrating IPv6 Into Your IPv4 Network. O'Reilly Media, Inc. pp. 222–223. ISBN 9781449335267.
^ "Advisory Guidelines for 6to4 Deployment". IETF. RFC 6343. Missing or empty|url=(help);|access-date=requires|url=(help)
^ "IPv6: Dual stack where you can; tunnel where you must". www.networkworld.com. 5 September 2007. Retrieved 27 November 2012.
^ "Basic Transition Mechanisms for IPv6 Hosts and Routers". IETF. RFC 4213. Missing or empty|url=(help);|access-date=requires|url=(help)
^ Silvia Hagen (2014). IPv6 Essentials: Integrating IPv6 Into Your IPv4 Network. O'Reilly Media, Inc. p. 222. ISBN 9781449335267.
^ Juniper TechLibrary (31 August 2017). "Understanding Dual Stacking of IPv4 and IPv6 Unicast Addresses". www.juniper.net. Retrieved 13 March 2017.
^ "IPv6". www.nro.net. Retrieved 13 March 2017.
^ Enric Pujol. "What stops IPv6 traffic in a dual-stack ISP?". www.apnic.net. Retrieved 13 Jun 2017.
^ Steven J. Vaughan-Nichols (14 October 2010). "Five ways for IPv6 and IPv4 to peacefully co-exist". www.zdnet.com. Retrieved 13 March 2017.
^ Silvia Hagen (2014). IPv6 Essentials: Integrating IPv6 Into Your IPv4 Network. O'Reilly Media, Inc. p. 33. ISBN 9781449335267.
^ "IP Version 6 Addressing Architecture". IETF. February 2006. RFC 4291. Retrieved 2017-11-28.
^ – OpenBSD Kernel Interfaces Manual
^ "Basic Socket Interface Extensions for IPv6". IETF. February 2003. p. 22. RFC 3493. Retrieved 2017-11-28.
^ "Web sites must support IPv6 by 2012, expert warns". Network World. 21 January 2010. Retrieved 30 September 2010.
^ "DOCSIS 2.0 Interface". Cablemodem.com. 29 October 2007. Archived from the original on 4 September 2009. Retrieved 31 August 2009.
^ "RMV6TF.org" (PDF). Archived from the original (PDF) on 5 January 2012. Retrieved 20 January 2012.
^ Mullins, Robert (April 5, 2012), Shadow Networks: an Unintended IPv6 Side Effect, retrieved March 2, 2013
^ Cicileo, Guillermo; Gagliano, Roque; O’Flaherty, Christian; et al. (October 2009). IPv6 For All: A Guide for IPv6 Usage and Application in Different Environments (PDF). p. 5. Retrieved March 2, 2013.
^ Jun-ichiro itojun Hagino (October 2003). "IPv4-Mapped Addresses on the Wire Considered Harmful".
^ "IPv4 Address Report". Potaroo.net. Retrieved 20 January 2012.
^ Mike Leber (2 October 2010). "Global IPv6 Deployment Progress Report". Hurricane Electric. Retrieved 19 October 2011.
^ "Beijing2008.cn leaps to next-generation Net" (Press release). The Beijing Organizing Committee for the Games of the XXIX Olympiad. 30 May 2008. Archived from the original on 4 February 2009.
^ Das, Kaushik (2008). "IPv6 and the 2008 Beijing Olympics". IPv6.com. Retrieved 15 August 2008.As thousands of engineers, technologists have worked for a significant time to perfect this (IPv6) technology, there is no doubt, this technology brings considerable promises but this is for the first time that it will showcase its strength when in use for such a mega-event.
^ Derek Morr (9 June 2009). "Verizon Mandates IPv6 Support for Next-Gen Cell Phones". CircleID.
^ theipv6guy (31 July 2012). "T-Mobile USA Launches External IPv6". T-Mobile. Archived from the original on 19 October 2013.
^ van Beijnum, Iljitsch. "IPv6 adoption starting to add up to real numbers: 0.6 percent". Ars Technica. Retrieved 9 April 2015.
^ David Frost (20 April 2011). "Ipv6 traffic volumes going backwards". iTWire. Retrieved 19 February 2012.
^ "Traffic Graphs | www.seattleix.net". www.seattleix.net. Retrieved 2017-10-30.
^ "Amsterdam Internet Exchange Ether Type". ams-ix.net. Retrieved 2015-10-06.
^ "IPv6". Google Statistics. Google. Retrieved 27 April 2015.
^ "Measurements | World IPv6 Launch". www.worldipv6launch.org. Retrieved 2018-11-19.
External links
| Wikiversity has learning resources about IPv6 |
IPv6 in the Linux Kernel by Rami Rosen.- Free Pool of IPv4 Address Space Depleted
- An Introduction and Statistics about IPV6